M+E Connections

STEGA CEO: Holistic Monitoring of Threats is Crucial for M&E Companies
Story Highlights
Holistic monitoring of security threats is important for media and entertainment companies to protect their infrastructures in offices, at homes and in the cloud, according to Phil Ashley, CEO of STEGA.
STEGA offers comprehensive cyber protection as-a-service that looks at the whole picture to deliver regular feedback to ensure an organisation is optimally protected, while working in the background to focus on the real threats it faces, he said 20th Oct. during the online Media & Entertainment Day event.
The firm is “proactive about mitigating threats that are out there” and works “in unity” with customers and partners to keep organisations protected, he pointed out during the Threat Vectors & Monitoring breakout session “Holistic Monitoring of Threats within M&E.”
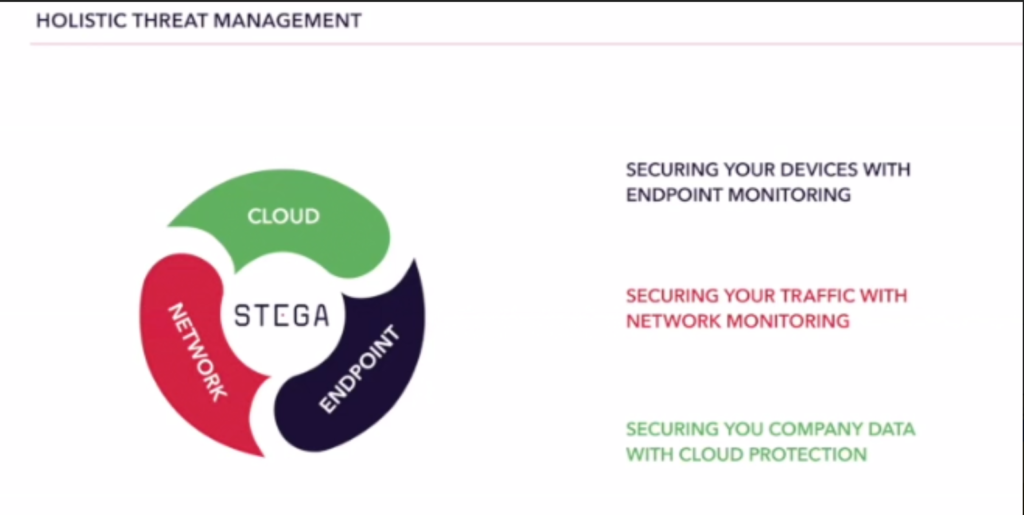
 Holistic threat management secures devices with endpoint monitoring, secures traffic with network monitoring, and secures a company’s data with cloud protection, he noted.
Holistic threat management secures devices with endpoint monitoring, secures traffic with network monitoring, and secures a company’s data with cloud protection, he noted.
“There’s a number of different components to this,” he said, explaining: “We start at the beginning and what we worry about is making sure that there’s enough protection and there’s involvement with all the systems and all the technologies and all the elements of a business that we work with…. It’s very important not to miss certain elements… because it creates gaps and it creates blind spots [otherwise]. So the first thing we worry about is actually making sure that there’s efficient visibility across all operations, wherever they may be. However, that is just sort of the start of the journey and the start of the puzzle.”
An expert security team: Prevents incidents from becoming breaches; understands threat context and motivation to be better equipped to defend against them; and provides advice and recommendations based on the threat landscape that an organisation faces, he noted.
“At the core of what we are trying to achieve is… understanding the nature of threats that… will be targeting potential organisations but really assess that risk as part and parcel of where they originate from and how… that risk [is] interpreted for any individual organisation,” he told viewers.
Ashley went on to explain that, “in any given month, looking across all the organisations that we look after,” it performs risk assessment “right down to the minor, minor details because a lot of that information is very, very important and very valuable.”
And “about half of all of those connections we assess as a risky connection,” he pointed out, noting: “The other half is fairly fine and innocuous…. If we look at domain information, even if we just look at registrations of domains, what we start to see is at least 30 percent, if not two-thirds or so of all of those domains are in some way… risky.”
 Meanwhile, “what we tend to see is about 5 percent or so of everything that we identify in some way as risky is actually on a public [black]list – so something that has been shared amongst the community that we’ve definitely identified as ‘This is bad. This is something that’s very known,’” he told viewers. That means “it’s a malicious IP address, it’s a malware host, it’s a botnet, it’s a particular piece of malware signature. So all of these elements are shared by many, many companies,” he said.
Meanwhile, “what we tend to see is about 5 percent or so of everything that we identify in some way as risky is actually on a public [black]list – so something that has been shared amongst the community that we’ve definitely identified as ‘This is bad. This is something that’s very known,’” he told viewers. That means “it’s a malicious IP address, it’s a malware host, it’s a botnet, it’s a particular piece of malware signature. So all of these elements are shared by many, many companies,” he said.
About 50 percent (52% to be exact) of that is “something that we have actively identified as nefarious,” meaning that “it’s been involved in some activity…. that we have seen is related to something that is not correct – is not normal behaviour and is definitely something that could potentially be malicious,” he explained.
About 52% each are identified as malicious association or mismatching information.
“The unknown malicious piece is one of the key areas that we have to focus on,” Ashley said, noting it is important to “use a lot of that threat intelligence as best as you possibly can to actually start making real informed decisions because most incidents where breaches are going to occur are going to be in these grey areas.”
The “real challenge that this presents” for M&E organisations, however, is “about two thirds of this information becomes irrelevant after about a month,” he warned, noting it tends to disappear in some way. There is a “very, very high churn rate,” he added. That is why it is crucial to work to keep information up to date. It is also best to deal with potential threats before they impact an organisation, he concluded.
Click here to access the full presentation.
M&E Day was sponsored by IBM Security, Microsoft Azure, SHIFT, Akamai, Cartesian, Chesapeake Systems, ContentArmor, Convergent Risks, Deluxe, Digital Nirvana, edgescan, EIDR, PK, Richey May Technology Solutions, STEGA, Synamedia and Signiant and was produced by MESA, in cooperation with NAB Show New York, and in association with the Content Delivery & Security Association (CDSA) and the Hollywood IT Society (HITS).









